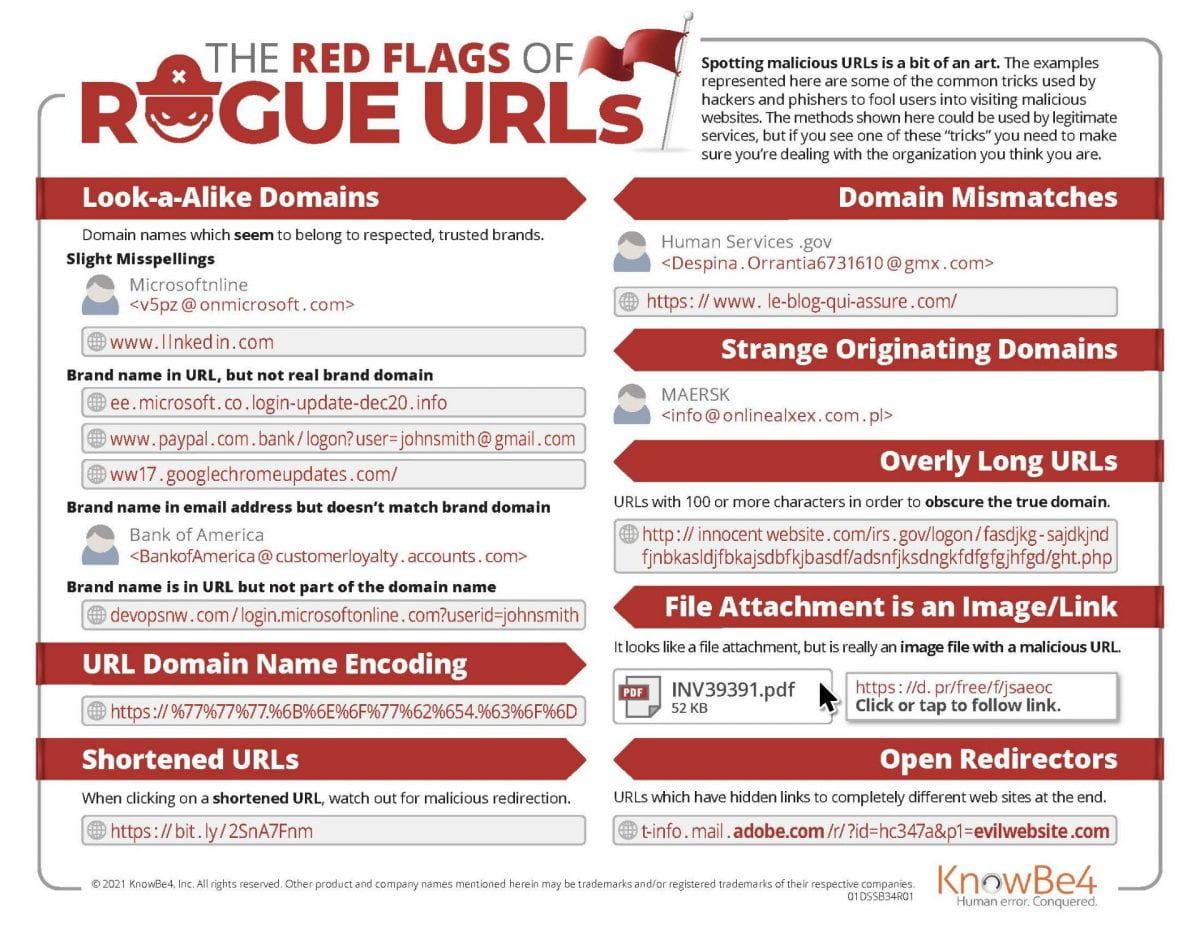
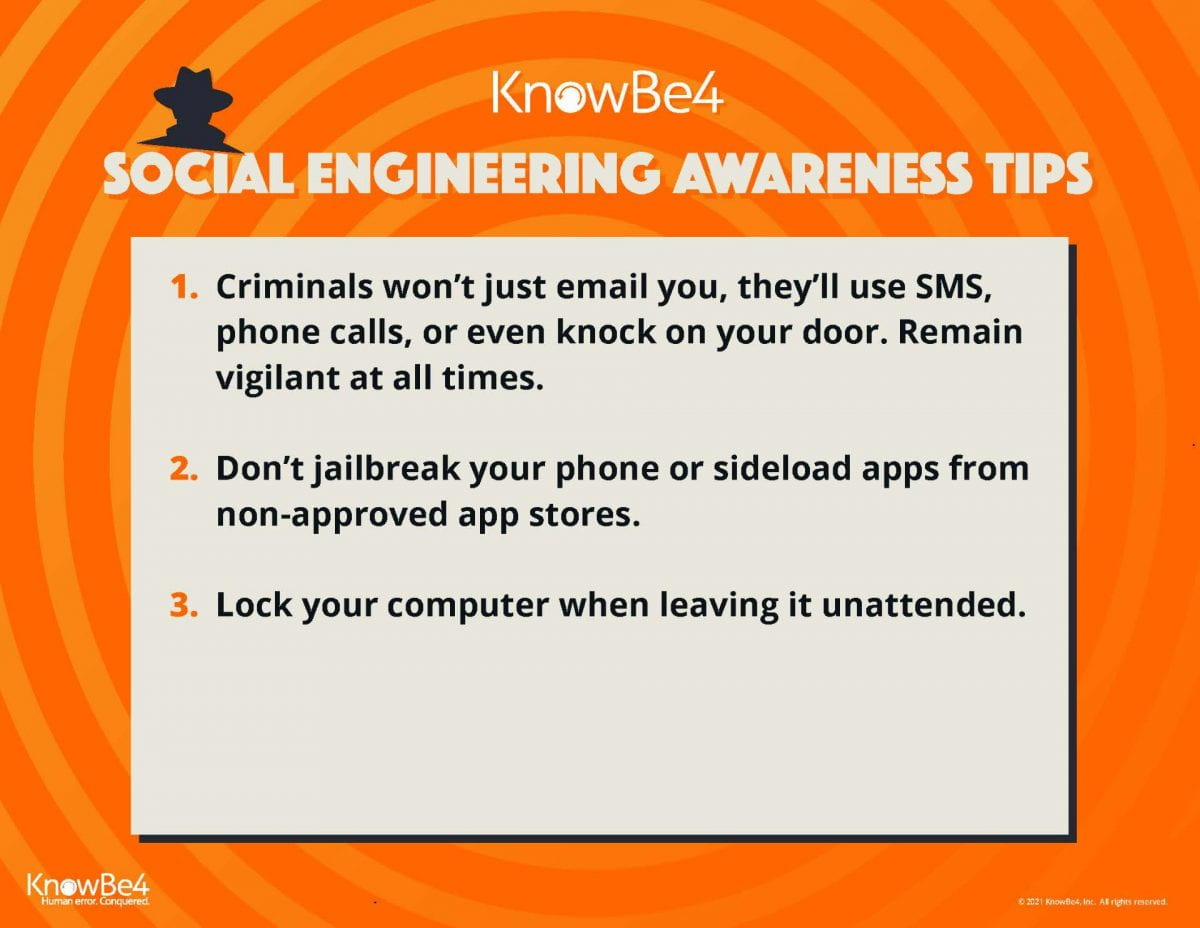
Today is International Stand Up to Bullying Day, a special semi-annual event in which participants wear and use pink to take a visible, public stance against bullying.
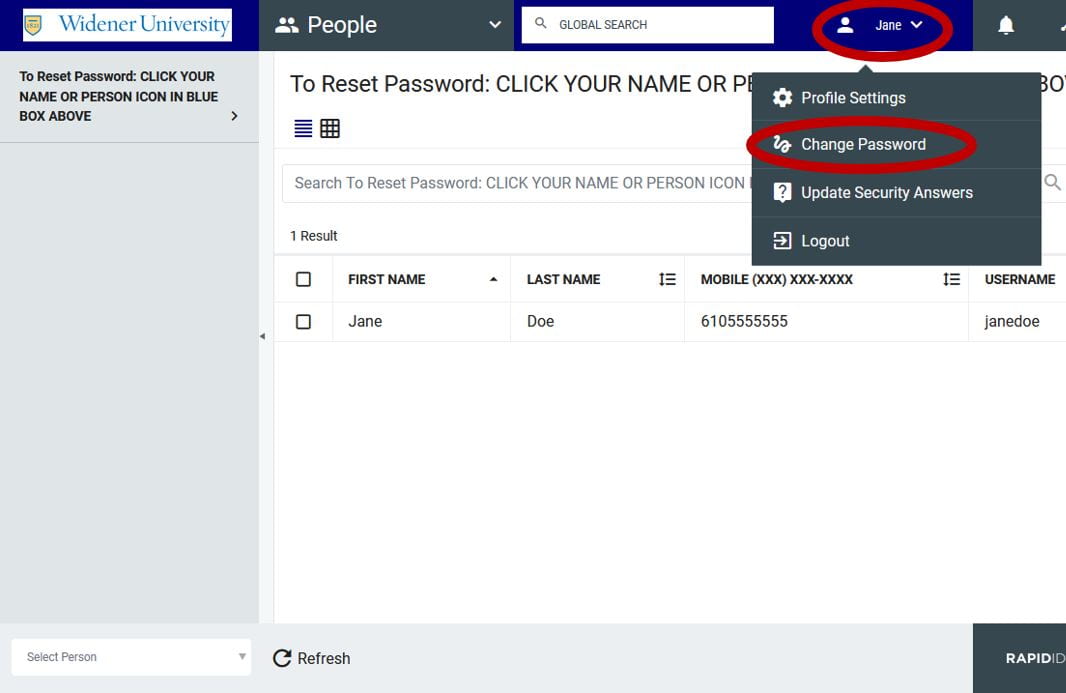
Stand up to bullying and show your support for your fellow members of the Pride, by using this pink Zoom background for your next class or meeting. The background has been added to Widener’s default Zoom backgrounds and available to select when choosing a virtual background. Don’t see it? Sign out of Zoom and then sign back in with the SSO option.
Cyberbullying vs. bullying
Cyberbullying is the “willful and repeated harm inflicted through the use of computers, cell phones, and other electronic devices” (from cyberbullying.org). These elements include the following:
-
-
-
- Willful: The behavior has to be deliberate.
- Repeated: Bullying reflects a pattern of behavior, not just one isolated incident.
- Harm: The target must perceive that harm was inflicted.
- Computers, cell phones, and other electronic devices: This, of course, is what differentiates cyberbullying from traditional bullying
Anonymity, Distance, and Scope
While often similar in terms of form and technique, the three main differences can make cyberbullying even more devastating: anonymity, distance, and scope.
Because they don’t need to physically confront their victim, the aggressor can hide behind an anonymous username and their target might never know the source of their torment. This anonymity can also embolden those who would never dream of bullying someone in real life. While acting from a physically distant location, the aggressor doesn’t have to see the immediate effects of their actions. Anonymity and distance allow cyberbullies to be crueler than they ever would be in person.
The scope of cyberbullying and the ability for those hurtful actions to go viral means that a large number of people can participate in the victimization. Technology’s global reach provides a limitless pool of potential targets, aggressors, and witnesses/bystanders. Victims cannot escape the eyes of their virtual audience, which amplifies their feelings of helplessness and despair.
Why Pink?
The color pink is used in connection with the original campaign started by Travis Price and David Shepherd, two students who took a stand for a fellow student who was bullied for wearing a pink shirt to school.
“David Shepherd, Travis Price and their teenage friends organized a high-school protest to wear pink in sympathy with a Grade 9 boy who was being bullied [for wearing a pink shirt]…[They] took a stand against bullying when they protested against the harassment of a new Grade 9 student by distributing pink T-shirts to all the boys in their school. ‘I learned that two people can come up with an idea, run with it, and it can do wonders,’ says Mr. Price, 17, who organized the pink protest. ‘Finally, someone stood up for a weaker kid.’ So Mr. Shepherd and some other headed off to a discount store and bought 50 pink tank tops. They sent out message to schoolmates that night, and the next morning they hauled the shirts to school in a plastic bag. As they stood in the foyer handing out the shirts, the bullied boy walked in. His face spoke volumes. ‘It looked like a huge weight was lifted off his shoulders,’ Mr. Price recalled. The bullies were never heard from again.”
— Globe & Mail
We’re all Widener
At Widener, the safety & well-being of our community is a top priority. If you have experienced or witnessed bullying, or other forms of discrimination or harassment, there are resources here to help:
Report It
Campus Safety
Counseling & Psychological Services (CAPS)
Student Success & Support