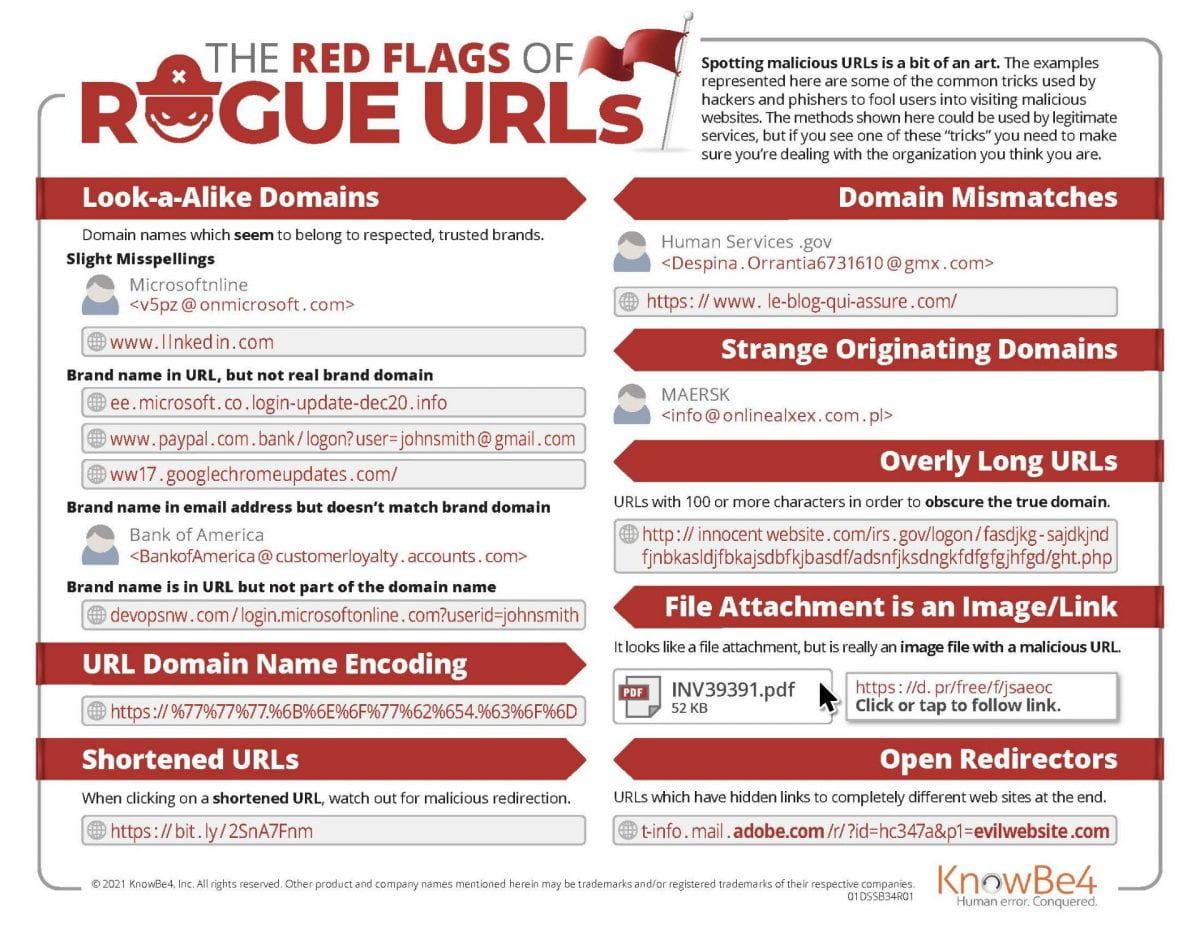
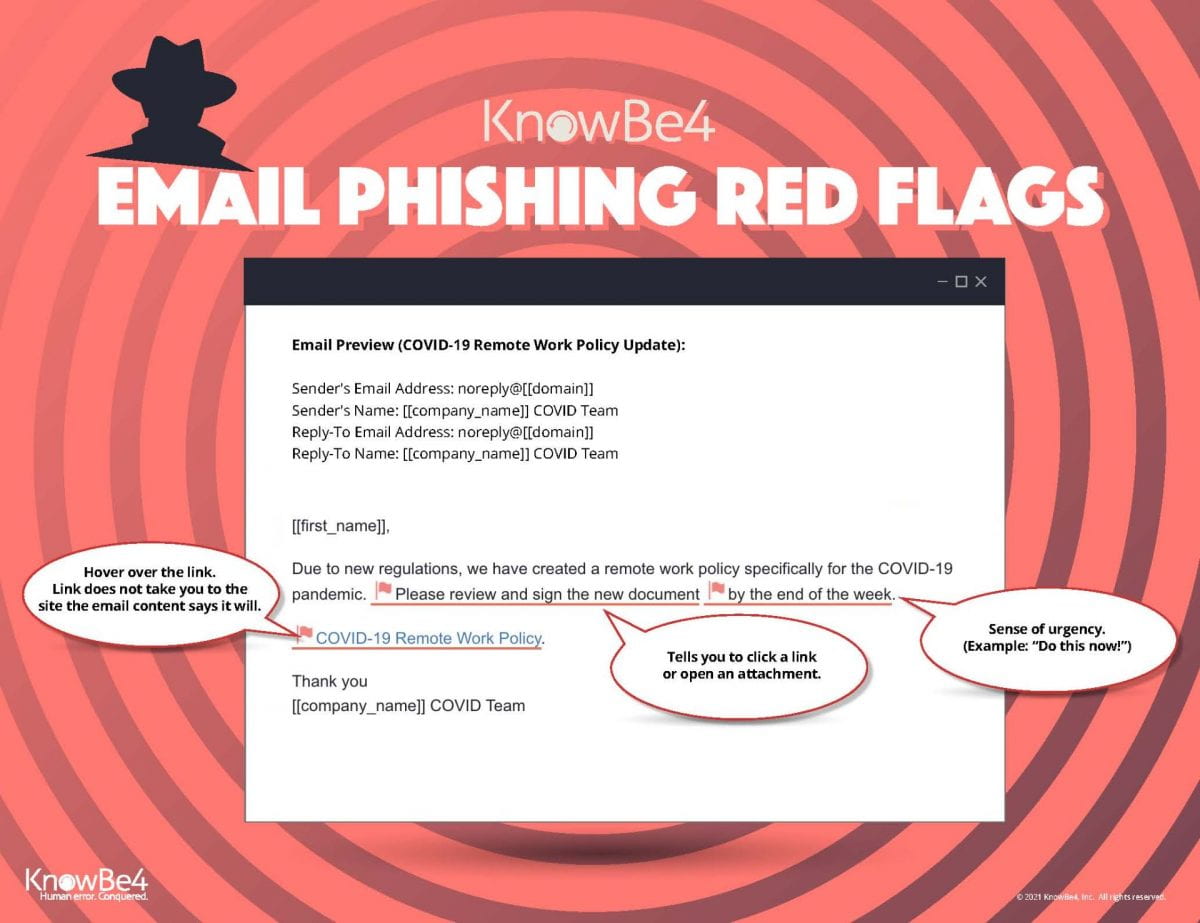
Microsoft Defender for Office 365
Widener LIS will be enabling Microsoft Defender for Office 365 on June 1st for Widener email (Outlook). All links that are found in an email are scanned by Office 365 protection services to check for security threats.
If an link is found to be unsafe, the user will be alerted with an interface describing the issue. If encountered, please close the web page immediately and continue on with your day knowing you were protected. If you feel like this website has been categorized by mistake, please open a quickticket and we will investigate. Using the “continue anyway” link is never recommended without the explicit direction of a member of the ITS Information Security Team.
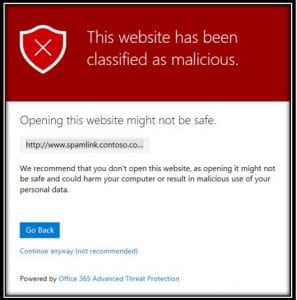
Safe Links
When a message contains a clickable image or text, the original address of the link will be replaced with a “safe link”. Safe links always contain the domain name “safelinks.protection.outlook.com/”. Safe links will show you the original URL when you hover over the link. Emails shown in plain text mode will show the full “safe link”.
Safe links will show you the original URL when you hover over the link. Emails shown in plain text mode will show the full “safe link”.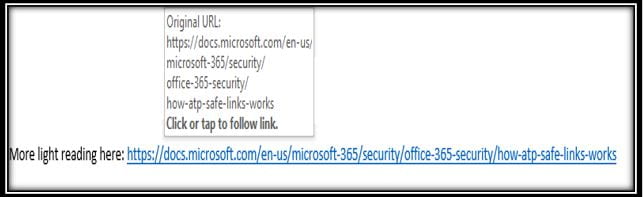
: : : : : : : : : : : : : : : : : : : : : : : : : : : : : : : :
If you have any questions, please open a quickticket.widener.edu or call the HelpDesk at 610-499-1047 for further assistance.