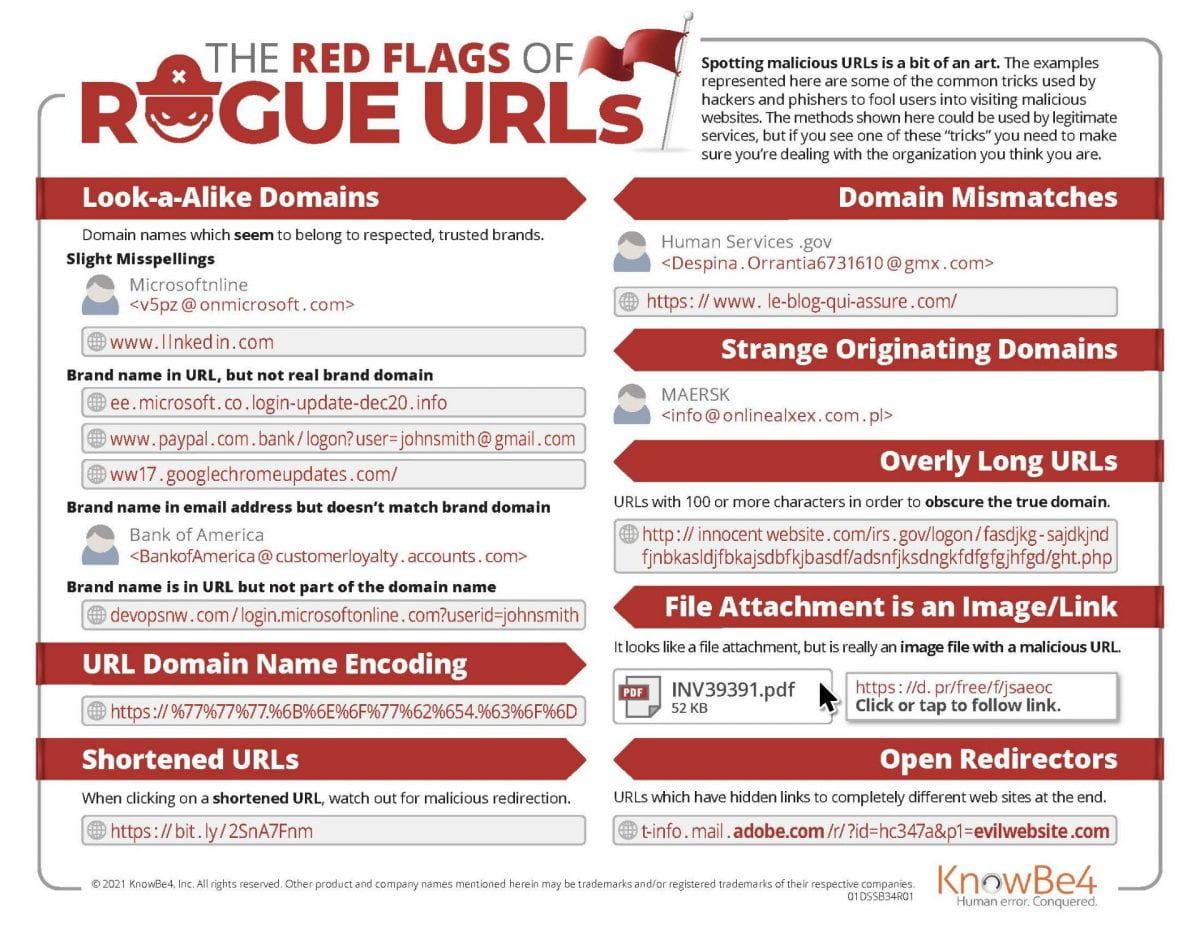
On March 16 2022, LIS will launch a newly updated user experience for PSS – Password Self Service.
Why are we doing this?
In order to keep PSS up to date with the latest security patches, we are required to perform an update. This update includes a new user interface for the desktop and mobile experience.
What can you expect in the new PSS?
You will notice that the new PSS features the same functionality as the old outdated version, just with a newly updated and streamlined user interface. Keep reading below for specifics on the differences that you will see.
How to change my password?
You still go https://pss.widener.edu and log in with your current credentials. Now click either your Name or the Person icon in the upper blue bar, then click Change Password.
Desktop Experience:
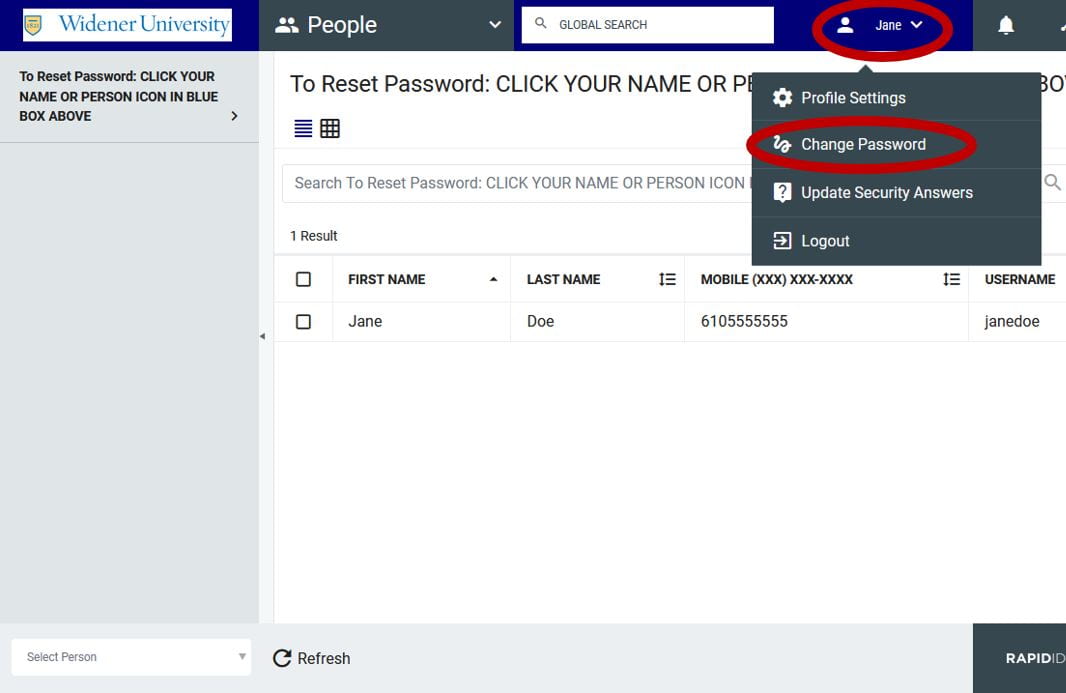
Mobile Experience:
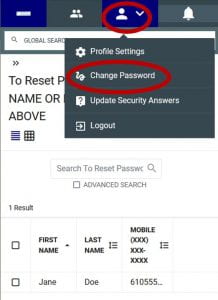
How do I change my cellphone number?
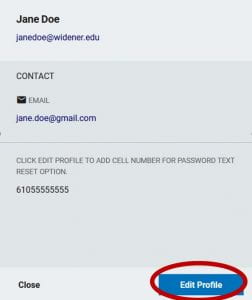
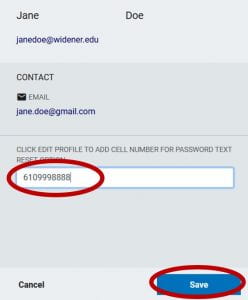
Login to https://pss.widener.edu, then click either your Name or the Person icon in the upper blue bar, then click Profile Settings. From here, click Edit Profile. Enter your new cellphone number (without the dashes) and click Save.
How do I change my Challenge Questions?
Login to https://pss.widener.edu, then click either your Name or the Person icon in the upper blue bar, then click Profile Settings. From here, click Update Security Questions. Here you have the ability to change your questions and/or answers.